A) zombie
B) rootkit
C) bot
D) Trojan horse
Correct Answer

verified
Correct Answer
verified
True/False
 -Online shopping sites generally use a session cookie to keep track of items in a user's shopping cart as shown in the accompanying figure.
-Online shopping sites generally use a session cookie to keep track of items in a user's shopping cart as shown in the accompanying figure.
Correct Answer

verified
Correct Answer
verified
True/False
Passwords and passphrases that are more than four characters, contain uppercase and lowercase letters, numbers, and special characters are the most secure.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following categories are the rights to which creators are entitled for their work?
A) community property
B) intellectual property
C) creative
D) ethical
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is an EULA intended to do?
A) license software for individual use
B) outline computer activities for which the computer and network may or may not be used
C) contract with an outside organization to provide security and recovery services for a network
D) establish a network of computers, such as a homegroup
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following laws provides the same protection that covers mail and telephone communications to electronic communications such as voice mail?
A) Electronic Communications Privacy Act (ECPA)
B) Fair Credit Reporting Act
C) Computer Fraud and Abuse Act
D) Computer Matching and Privacy Protection Act
Correct Answer

verified
Correct Answer
verified
Multiple Choice
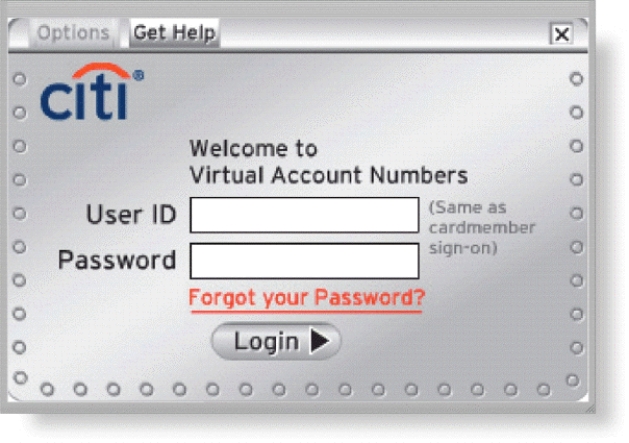 -Many websites, like that in the accompanying figure, require a user to enter a private combination of characters associated with a user name that allows access to certain computer resources. What is the term for this combination of characters?
-Many websites, like that in the accompanying figure, require a user to enter a private combination of characters associated with a user name that allows access to certain computer resources. What is the term for this combination of characters?
A) PIN
B) password
C) secure key
D) passterm
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What happens during a DDoS attack?
A) An unsuspecting computer is used to send an influx of confusing data messages or useless network traffic.
B) Antivirus software disables a virus and protects the computer or network from unauthorized access.
C) The police use a virus and other measures to take down a network of computer criminals.
D) A zombie army is used to attack computers or computer networks.
Correct Answer

verified
Correct Answer
verified
True/False
Biometric objects are entirely foolproof.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What occurs when someone steals personal or confidential information?
A) information theft
B) corruption
C) fraud
D) compaction
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Many businesses use which of the following to limit employees' web access?
A) content filtering
B) web bugs
C) honeypots
D) spyware
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What term is used to describe the discovery, collection, and analysis of evidence found on computers and networks?
A) cybersleuthing
B) digital forensics
C) system analysis
D) data mining
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Identify the letter of the choice that best matches the phrase or definition. -Biometric device used in high security areas.
A) digital signature
B) digital certificate
C) CA
D) digital security risk
E) firewall
F) botnet
G) zombie
H) clickjacking
I) Digital Millennium Copyright Act (DCMA)
J) DoS attack
K) AUP
L) iris recognition system
M) web filtering software
N) password
O) script kiddie
P) ciphertext
Q) plaintext
R) bot
S) piracy
T) copyright
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The term, payload, as it pertains to computer crime, is defined as _____________.
A) the money a criminal receives from extortion or other computer crimes
B) the amount of data loss to a company or individual who is a victim of a computer crime
C) the destructive event or prank the program is intended to deliver
D) the financial burden computer crime places on its victims
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Social engineering, as it pertains to computers, is _____________.
A) creating consumer and personal profiles by tracking website history and electronic purchases
B) compiling data from multiple computer users in order to make predictions about computer trends
C) filtering Internet content to targeted users based on their personal preferences
D) gaining unauthorized access or obtaining confidential information by taking advantage of the trusting nature or naivety of users
Correct Answer

verified
Correct Answer
verified
True/False
Proximity sharing gives websites access to your current location.
Correct Answer

verified
Correct Answer
verified
True/False
Cybercrime laws are consistent between states and countries, making it easy to reach a consensus as to what is illegal.
Correct Answer

verified
Correct Answer
verified
Short Answer
____________________ involves the examination of media, programs, data and log files on computers, mobile devices, servers, and networks.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You have just provided the identification number that associates your new software purchase with the mobile device on which you installed the software. What is the term for this process?
A) software deployment
B) software decryption
C) app installation
D) product activation
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Identify the letter of the choice that best matches the phrase or definition. -An authorized person or company that issues and verifies digital certificates.
A) digital signature
B) digital certificate
C) CA
D) digital security risk
E) firewall
F) botnet
G) zombie
H) clickjacking
I) Digital Millennium Copyright Act (DCMA)
J) DoS attack
K) AUP
L) iris recognition system
M) web filtering software
N) password
O) script kiddie
P) ciphertext
Q) plaintext
R) bot
S) piracy
T) copyright
Correct Answer

verified
Correct Answer
verified
Showing 101 - 120 of 197
Related Exams