A) Type 3
B) Type 4
C) Type 1
D) Type 2
E) Type 5
Correct Answer

verified
Correct Answer
verified
True/False
To configure AAA, you need to configure a RADIUS server as follows: [Huawei]radius-server template EXAM [Huawei-radius-EXAM]radius-server shared-key cipher HUAwei123 [Huawei-radius-EXAM]radius-server authentication 10.7.66.66 1812 [Huawei-radius-EXAM]radius-server authorization 10.7.66.66 1812 [Huawei-radius-EXAM]radius-server accounting 10.7.66.66 1813 [Huawei-radius-EXAM]radius-server retransmit 2
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Two community filters are configured as follows: ip community-filter 1 permit 100:1 200:1 ip community-filter 2 permit 100:1 ip community-filter 2 permit 200:1 Which of the following statements regarding the community filters are true? (Choose two.)
A) A BGP route matches community-filter 2 only when it carries the Community attribute values of 100:1 and 200:1.
B) A BGP route matches community-filter 1 only when it carries the Community attribute value of 100:1 or 200:1, or both.
C) A BGP route matches community-filter 1 only when it carries the Community attribute values of 100:1 and 200:1.
D) A BGP route matches community-filter 2 only when it carries the Community attribute values of 100:1 and 200:1, or both.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Source Specific Multicast (SSM) is being used throughput the HW IP Multicast network. Which of the following three statements about SSM are true? (Choose three.)
A) SSM uses Shortest-Path Trees Only
B) There are no RPs to worry about
C) SSM is best suited for applications that are of the Many-to-Many category
D) SSM uses shared Trees only
E) The use of SSM is recommended when there are many sources and it is desirable to keep the amount of mroute state in the routers in the network to a minimum.
F) SSM is best suited for applications that are of one-to-many category
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Why does RSTP achieve faster convergence than STP?
A) RSTP convergence is not based on the timer mechanism
B) RSTP has a smaller cost value
C) RSTP has additional port states
D) RSTP has a smaller timer value
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The IS-IS overload bit is set on R3. Which of the following statements are true? (Choose three.) 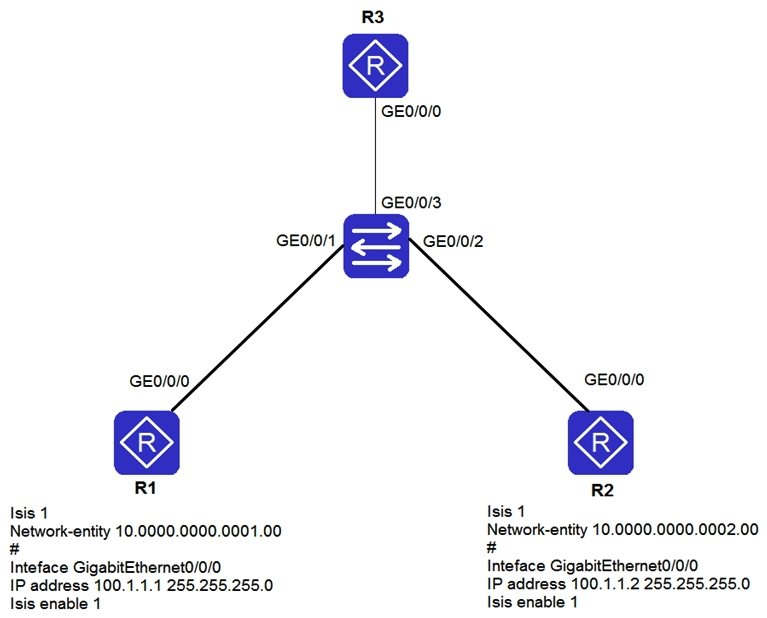
A) Before the timeout of the overload timer on R3, R1 and R2 do not add the LSPs generated by R3 to the SPF tree.
B) The direct route of R3 is ignored by R1 and R2 due to the setting of the overload bit.
C) LSPs of R3 cannot be flooded to R1 and R2.
D) Routes imported to R3 through the import-route command cannot be advertised.
E) When a router is experiencing a memory shortage, the system automatically sets the overload bit in the sent LSPs regardless of whether you have the set-overload command.
Correct Answer

verified
Correct Answer
verified
True/False
As shown in the figure, the routers load balances the traffic between Branch network 1 and Branch network 2. In this case, URPF in loose mode must be configured on a physical interface to defend against attacks using spoofed source IP addresses. 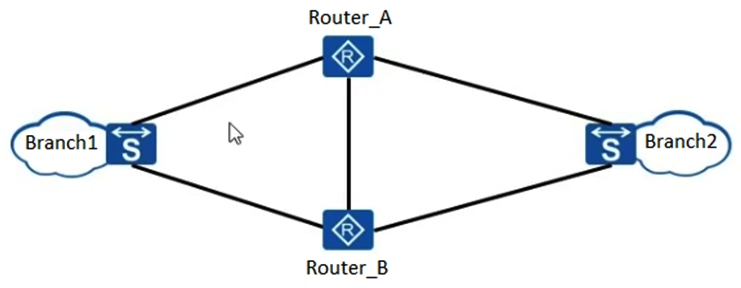
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following statements regarding the process in which the source DR registers with the RP on a PIM-SM network is true?
A) The Register message is a multicast packet
B) The Register message is used to set up an RPT between the source DR and RP
C) After receiving the Register message, the RP sends a Register-Stop message
D) The Register message carries multicast service data
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Two routers configured to run BGP have been connected to a firewall, one on the inside interface and one on the outside interface. BGP has been configured so the two routers should peer, including the correct BGP session endpoint addresses and the correct BGP session hop-count limit (EBGP multihop) . What is a good first test to see if BGP will work across the firewall?
A) There is no way to make BGP work across a firewall without special configuration, so there is no simple test that will show you if BGP will work, other than trying to start the peering session.
B) Attempt to Telnet from the router connected to the inside of the firewall to the router connected to the outside of the firewall. If Telnet works, BGP will work, since telnet and BGP both use TCP to transport data
C) There is no way to make BGP work across a firewall
D) Ping from the router connected to the inside interface of the firewall to the router connected to the outside interface of the firewall. If you can ping between them, BGP should work, since BGP uses IP to transport packets.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Based on the key configurations, as shown in the figure, R1 and R2 establish a Level-2 neighbor relationship. Which of the following statements regarding routing entries on R2 are true? 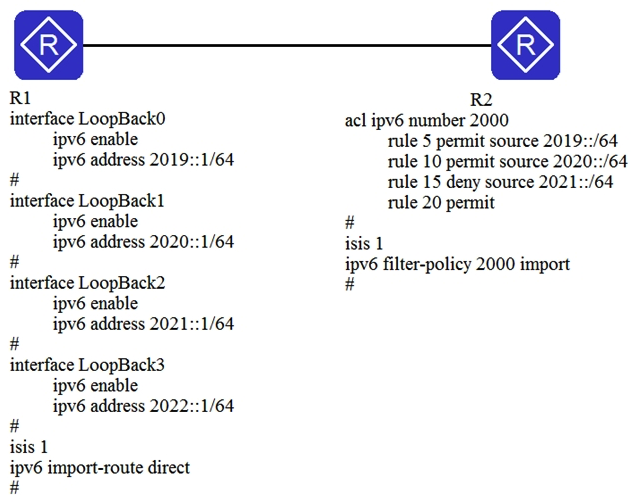
A) 2020:: /64 will be displayed in the IP routing table.
B) 2021:: /64 will be displayed in the IP routing table.
C) 2019:: /64 will not be displayed in the IP routing table.
D) 2022:: /64 will not be displayed in the IP routing table.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
On the network shown in the figure below, SW1, SW2 and SW3 are deployed. SW1 is the root bridge, link congestion occurs between SW1 and SW2, and SW2 cannot receive configuration BPDUs sent by the root bridge. Given this information, which of the following spanning tree protection mechanisms needs to be configured to prevent problems caused by link congestion? 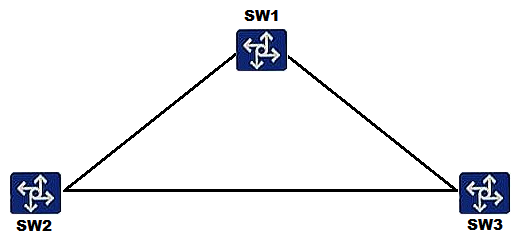
A) Defense against TC BPDU attacks
B) Root protection
C) BPDU protection
D) Loop protection
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following attributes cannot be directly referenced by the if-match clause of route-policies?
A) Community-filter
B) IP-prefix
C) AS-Path-filter
D) Regular expression
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following statements regarding BGP attributes is true?
A) A route can have only one value for the Community attribute.
B) The number of the neighboring AS is displayed to the right of the AS_path list of a BGP routing entry.
C) The Local_Pref attribute is exchanged only between EBGP peers and is not advertised other Ass.
D) When advertising a route learned from an EBGP peer to an IBGP peer, the BGP speaker does not change the Next_Hop attribute of the route.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following statements regarding the processing of BPDUs in 802.1w and 802.1D is true?
A) In 802.1D, the bridge only forwards the BPDUs received from the root bridge
B) In 802.1w, the bridge only forwards the BPDUs received from the root bridge
C) In 802.1D, the bridge does not forward BPDUs
D) In 802.1w, the bridge does not forward BPDUs
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which types of prefixes will a router running BGP most likely advertise to an IBGP peer, assuming it is not configured as a route reflector?
A) Prefixes received from EBGP peers and prefixes received from route reflectors
B) All prefixes in its routing table
C) Prefixes received from EBGP peers and prefixes locally originated via network statements or imported
D) Prefixes received from other IBGP peers, prefixes received from EBGP peers, and prefixes imported to BGP
E) Prefixes received from other IBGP peers and prefixes received from router reflectors
F) Prefixes received from any other BGP peer and prefixes locally originated via network statements or imported
Correct Answer

verified
Correct Answer
verified
Multiple Choice
On a BGP/MPLS Ipv4 VPN, OSPF, LDP, and static routes are configured. Which of the following protocols must be enabled with GR to achieve NSF on PEs?
A) Static routes
B) MPLS LDP
C) OSPF
D) BGP
Correct Answer

verified
Correct Answer
verified
Multiple Choice
On a RIPng network, configure a router to advertise the default route to the entire network. Which of the following configurations is correct?
A) [Huawei]ripng 1 [Huawei-ripng-1]import-route static cost 2 [Huawei-ripng-1]quit [Huawei]ipv6 route-static :: 0 NULL0
B) [Huawei]ipv6 route-static :: 0 2001:19:9
C) [Huawei-ripng-1] ripng default-route originate [Huawei-ripng-1]quit
D) [Huawei]interface GigabitEthernet0/0/1 [Huawei-GigabitEthernet0/0/1]ipv6 enable [Huawei-GigabitEthernet0/0/1]ipv6 address 2001::12::1/64 [Huawei-GigabitEthernet0/0/1]ripng 1 enable [Huawei-GigabitEthernet0/0/1]ripng default-route originate [Huawei-GigabitEthernet0/0/1]quit
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following technologies can be used to improve the MPLS BGP VPN reliability?
A) VPN GR
B) FRR for private IP routes between Pes and CEs
C) VPN FRR
D) CE dual-homing networking at the access layer
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The figures below show an enterprise's Layer 2 networking architecture and information displayed when engineers check the device status after communication between departments fails. 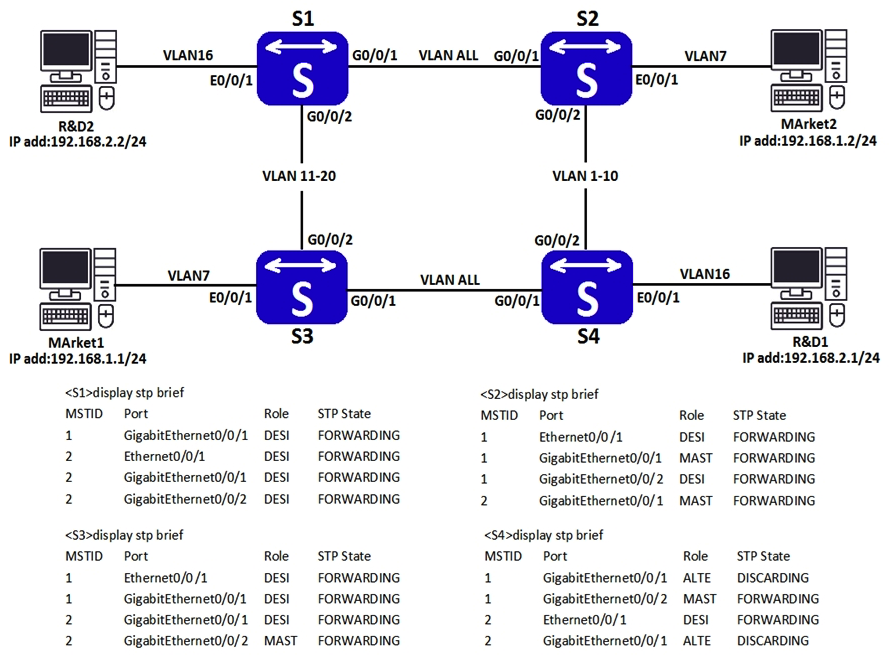 What are the possible causes of this communication failure?
What are the possible causes of this communication failure?
A) The switches have different region names.
B) The switches have different instance-VLAN mapping configurations.
C) The switches have different revision levels.
D) The switches have different BPDU sending intervals.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A family user has subscribed to a bandwidth of 10 Mbit/s. To improve user experience, the carrier ensures a rate of 12 Mbit/s during tests. If token bucket technology is used to cope with this requirement, which of the following methods is optimal?
A) cir 10000 cbs 12000 pbs 12000
B) cir 8000 pir 12000
C) cir 10000 pir 12000
D) cir 10000 cbs 10000 pbs 12000
Correct Answer

verified
Correct Answer
verified
Showing 141 - 160 of 331
Related Exams