A) Implement a tabular structure.
B) Gather files in a distributed repository.
C) Use a hierarchical database file system.
D) Tightly couple database structure to database application programs.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which mechanism provides database users with controlled access to the database through the use of virtual tables?
A) View
B) Data dictionary
C) Database control language
D) Database management system
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following definitions best describes an entity?
A) A relation
B) Data about data
C) Data stored in a table column
D) An item about which information is stored
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Your company must choose which type of database to use for a new project. Which of the following lists three characteristics of file-based database systems?
A) Repetition of data, application program flexibility, and data centralization
B) Incompatibility of files, tabular data structures, and data dependence
C) Separation of data, repetition of data, and data independence
D) Application program inflexibility, data dependence, and separation of data
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Consider the table shown in the exhibit. Which relational algebraic operation would return Row 3? 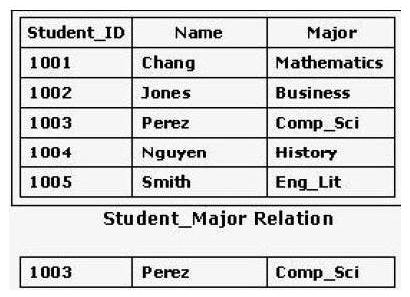
A) Union
B) Selection
C) Projection
D) Difference
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the highest normal form of the relation(s) shown in the exhibit? 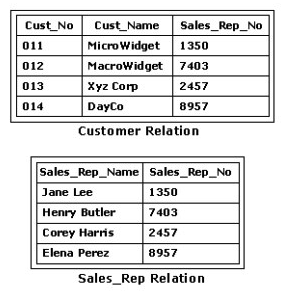
A) No normal form
B) Second normal form
C) First normal form
D) Third normal form
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is a characteristic of the three-tier database architecture?
A) A Web browser is used as the application server.
B) The application logic is centralized on a dedicated server.
C) A thick client is used to perform business application logic functions locally.
D) Database application logic and database functionality are integrated and reside on a common server.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Consider the Orders relation shown in the exhibit. Which of the following SQL statements would replace the value in the Sales_Rep_No column with 110 everywhere that Sales_Rep_No 108 is listed? 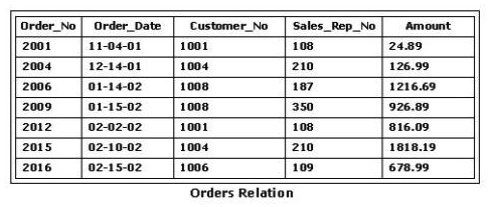
A) UPDATE Sales_Rep_No IN Orders SET(Sales_Rep_No = 110 WHERE Sales_Rep_No = 108) ;
B) UPDATE Orders SET Sales_Rep_No = 110 WHERE Sales_Rep_No = 108;
C) SET Sales_Rep_No = 110;
D) WHERE Sales_Rep_No = 108
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Your database administrator has disallowed a group of users from making alterations to the Employees table in your corporate database. The users, known as Group_2, previously had full privileges with the Employees table. Which of the following SQL statements properly removes any alteration privileges from Group_2?
A) REVOKE INSERT, UPDATE, DELETE ON Employees FROM Group_2;
B) REVOKE UPDATE FOR Employees FROM Group_2;
C) Employees FOR Group_2;
D) UPDATE, DELETE FOR Employees
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Consider the Employee relation shown in the exhibit. A database manager wants to set up a view called Emp_Dept that allows users to find employees and their department ID numbers. Which SQL statement will accomplish this? 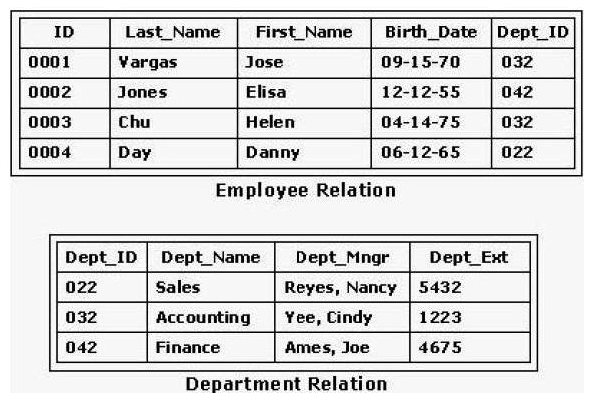
A) CREATE VIEW Emp_Dept AS SELECT Last_Name, First_Name, Dept_ID FROM Employee;
B) UPDATE VIEW Emp_Dept AS SELECT * FROM
C) UPDATE VIEW Emp_Dept AS SELECT
D) CREATE VIEW Emp_Dept Employee WHERE ID = 0001 AND ID = 0002 AND ID = 0003 AND ID = 0004;
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Consider the Project relation shown in the exhibit as well as the following SQL statement: DELETE FROM Project WHERE Cust_Name = Acme; Which of the following tables shows the Project relation after execution of this SQL statement? 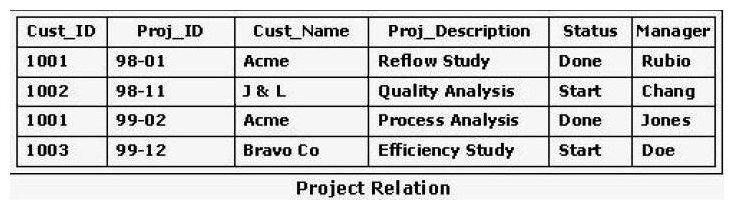
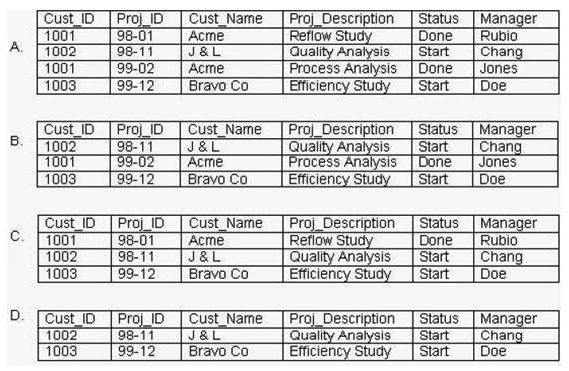
A) Option A
B) Option B
C) Option C
D) Option D
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which database architecture is best suited to implementation in the World Wide Web environment?
A) Two-tier using thin client
B) Three-tier using fat client
C) Three-tier using thin client
D) Centralized mainframe with terminal client
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Your enterprise is developing a database system that will contain highly sensitive data. Security of the data will take priority over database processing speed. Which database protection technique should be employed?
A) Backups
B) User views
C) Encryption
D) Integrity controls
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which type of relational integrity is violated if a primary key in a database has a null value?
A) Entity integrity
B) Domain integrity
C) Domain constraints
D) Referential integrity
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The database manager wants to give Rubio and Doe the ability to modify the Project Relation shown in the exhibit. A temporary employee named Temp needs to access the data in the database to generate reports. Which group of SQL statements will perform this task? 
A) GRANT UPDATE ON Project TO Rubio, Doe; GRANT SELECT ON Project TO Temp;
B) GRANT ALL PRIVILEGES ON Project TO Rubio, Doe; GRANT UPDATE ON Project TO Temp;
C) GRANT SELECT ON Project WHERE Manager = 'Rubio'; WHERE Manager = 'Doe';
D) GRANT UPDATE ON Project
Correct Answer

verified
Correct Answer
verified
Showing 61 - 75 of 75
Related Exams