A) User Center
B) Package repository
C) Download Center Web site
D) License and Contract repository
Correct Answer

verified
Correct Answer
verified
Multiple Choice
To ensure that VMAC mode is enabled, which CLI command you should run on all cluster members? Choose the best answer.
A) fw ctl set int fwha vmac global param enabled
B) fw ctl get int fwha vmac global param enabled; result of command should return value 1
C) cphaprob -a if
D) fw ctl get int fwha_vmac_global_param_enabled; result of command should return value 1
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the benefit of Manual NAT over Automatic NAT?
A) If you create a new Security Policy, the Manual NAT rules will be transferred to this new policy
B) There is no benefit since Automatic NAT has in any case higher priority over Manual NAT
C) You have the full control about the priority of the NAT rules
D) On IPSO and GAIA Gateways, it is handled in a Stateful manner
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Fill in the blank: Licenses can be added to the License and Contract repository ________ .
A) From the User Center, from a file, or manually
B) From a file, manually, or from SmartView Monitor
C) Manually, from SmartView Monitor, or from the User Center
D) From SmartView Monitor, from the User Center, or from a file
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You noticed that CPU cores on the Security Gateway are usually 100% utilized and many packets were dropped. You don't have a budget to perform a hardware upgrade at this time. To optimize drops you decide to use Priority Queues and fully enable Dynamic Dispatcher. How can you enable them?
A) fw ctl multik dynamic_dispatching on
B) fw ctl multik dynamic_dispatching set_mode 9
C) fw ctl multik set_mode 9
D) fw ctl miltik pq enable
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Jack works for a managed service provider and he has been tasked to create 17 new policies for several new customers. He does not have much time. What is the BEST way to do this with R80 security management?
A) Create a text-file with mgmt_cli script that creates all objects and policies. Open the file in SmartConsole Command Line to run it. Create a text-file with mgmt_cli script that creates all objects and policies. Open the file in SmartConsole Command Line to run it.
B) Create a text-file with Gaia CLI -commands in order to create all objects and policies. Run the file in CLISH with command load configuration . Create a text-file with Gaia CLI -commands in order to create all objects and policies. Run the file in CLISH with command load configuration .
C) Create a text-file with DBEDIT script that creates all objects and policies. Run the file in the command line of the management server using command dbedit -f . Create a text-file with DBEDIT script that creates all objects and policies. Run the file in the command line of the management server using command dbedit -f
D) Use Object Explorer in SmartConsole to create the objects and Manage Policies from the menu to create the policies.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are the senior Firewall administrator for Alpha Corp, and have recently returned from a training course on Check Point's new advanced R80 management platform. You are presenting an in-house overview of the new features of Check Point R80 Management to the other administrators in Alpha Corp. 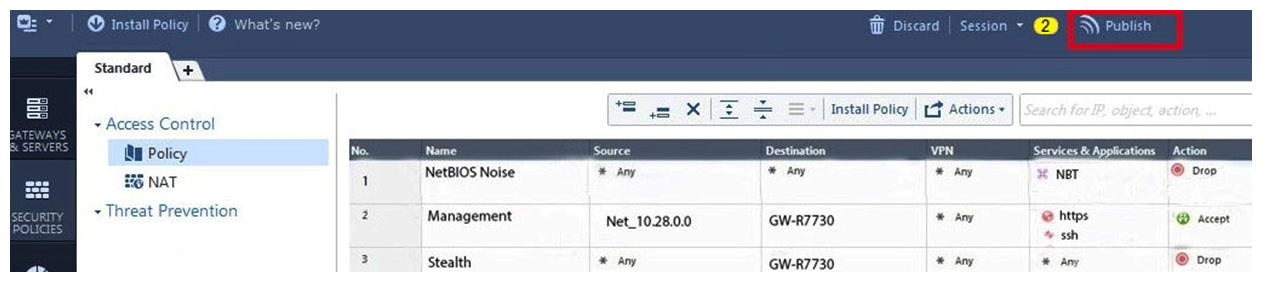 How will you describe the new " Publish " button in R80 Management Console?
How will you describe the new " Publish " button in R80 Management Console?
A) The Publish button takes any changes an administrator has made in their management session, publishes a copy to the Check Point Cloud of R80, and then saves it to the R80 database.
B) The Publish button takes any changes an administrator has made in their management session and publishes a copy to the Check Point Cloud of R80 and but does not save it to the R80 database.
C) The Publish button saves any changes an administrator has made in their management session. After saving to the database, any changes are now visible to all other administrator sessions.
D) The Publish button saves any changes an administrator has made in their management session. After saving to the database, any changes are now visible to any new Unified Policy sessions.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
To enforce the Security Policy correctly, a Security Gateway requires:
A) a routing table
B) that each Security Gateway enforces at least one rule
C) a Demilitarized Zone
D) a Security Policy install
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Fill in the blank: An Endpoint identity agent uses a ___________ for user authentication.
A) Shared secret
B) Token
C) Username/password or Kerberos Ticket
D) Certificate
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You can see the following graphic: 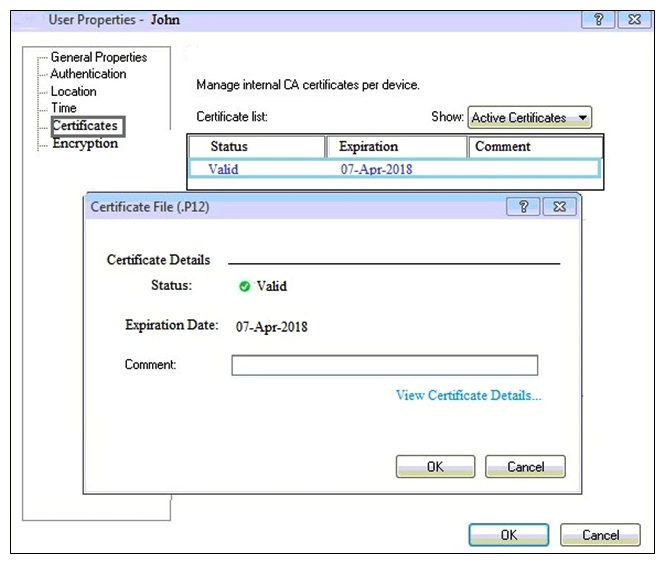 What is presented on it?
What is presented on it?
A) Properties of personal .p12 certificate file issued for user John.
B) Shared secret properties of John's password.
C) VPN certificate properties of the John's gateway.
D) Expired .p12 certificate properties for user John.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Where can you trigger a failover of the cluster members? 1. Log in to Security Gateway CLI and run command clusterXL_admin down . 2. In SmartView Monitor right-click the Security Gateway member and select Cluster member down 3. Log into Security Gateway CLI and run command cphaprob down
A) 1, 2, and 3
B) 2 and 3
C) 1 and 2
D) 1 and 3
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is NOT an authentication scheme used for accounts created through SmartConsole?
A) Security questions
B) Check Point password
C) SecurID
D) RADIUS
Correct Answer

verified
Correct Answer
verified
Multiple Choice
In R80, more than one administrator can login to the Security Management Server with SmartConsole with write permission at the same time.
A) False, this feature has to be enabled in the Global Properties.
B) True, every administrator works in a session that is independent of the other administrators.
C) True, every administrator works on a different database that is independent of the other administrators.
D) False, only one administrator can login with write permission.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
In R80 spoofing is defined as a method of:
A) Disguising an illegal IP address behind an authorized IP address through Port Address Translation.
B) Hiding your firewall from unauthorized users.
C) Detecting people using false or wrong authentication logins
D) Making packets appear as if they come from an authorized IP address.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Where is the "Hit Count" feature enabled or disabled in SmartConsole?
A) On the Policy Package
B) On each Security Gateway
C) On the Policy layer
D) In Global Properties for the Security Management Server
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the command to see cluster status in cli expert mode?
A) fw ctl stat
B) clusterXL stat
C) clusterXL status
D) cphaprob stat
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What does the "unknown" SIC status shown on SmartConsole mean?
A) The SMS can contact the Security Gateway but cannot establish Secure Internal Communication.
B) SIC activation key requires a reset.
C) The SIC activation key is not known by any administrator.
D) There is no connection between the Security Gateway and SMS.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The organization's security manager wishes to back up just the Gaia operating system parameters. Which command can be used to back up only Gaia operating system parameters like interface details, Static routes and Proxy ARP entries?
A) save configuration
B) backup
C) migrate export
D) upgrade export
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the Manual Client Authentication TELNET port?
A) 23
B) 264
C) 900
D) 259
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which software blade does NOT accompany the Threat Prevention policy?
A) Anti-virus
B) IPS
C) Threat Emulation
D) Application Control and URL Filtering
Correct Answer

verified
Correct Answer
verified
Showing 301 - 320 of 676
Related Exams